By Christian Rentrop and Markus Will
One of the biggest truisms of the Internet is that e-mails are like postcards: anyone can read them on the go - and therefore no confidential information should be passed on here. The reason for this is that an e-mail is not simply exchanged between the sender and recipient: On the way it can happen that it is routed through numerous servers and countries - even if the recipient lives two houses next door. The reason: The large free mail providers such as Google, Apple or Microsoft, but also many others, use US servers. In case of doubt, the general structure of the Internet itself ensures the countless diversions and servers on the way. Servers on which a malicious admin can theoretically sit and intercept or read the mail.
Reason enough to think about email encryption.
Encrypt emails: here's how
- Install a mail program such as Thunderbird, Apple Mail or Outlook.
- Set up your email address there . You can get the setup data from your mail provider, who usually has an FAQ or a website such as Gmail here https://support.google.com/mail/answer/7126229?hl=de , GMX here https: // help .gmx.net / pop-imap / imap / index.html or Microsoft Live here https://support.microsoft.com/de-de/help/287604/configure-outlook-to-connect-to-an-msn- email account .
- Now download a GnuPG client , such as GPG4Win for Outlook, CygWin, Enigmail or the GPGTools for Mac.
- After installation, these programs offer the option of generating a key pair for each e-mail address specified in the mail client.
- You have to enter a password . This is intended to ensure that there is still protection in the event that the key does get into the wrong hands. You should be careful not to forget it, otherwise the key can no longer be used.
- You can then upload your public key to the key server . There is a worldwide PGP server group of networked servers on which the public key is uploaded to make it easier to access. Someone can now send you an encrypted or signed message if they can find your key there. You can also put the public key on your website or attach it to your emails.
- You must protect and secure the private key before you can open this message. It is also advisable to keep the private key locked away from third parties, regardless of the computer. It is also important to create a revocation certificate. This is used if your key is compromised or the private key is no longer in your possession. This means that the key on the PGP servers can be set to "invalid" without having to use the private key. In this way you avoid a "file file", since the keys cannot in principle be deleted there.
- The OpenPGP program in the mail program automatically recognizes when you have received an encrypted e-mail.
- You can send encrypted mail if you know the recipient's public key . Modern GnuPG clients check this automatically using the email address.
- You still have all the freedom: Just because you now have a PGP key, you don't have to encrypt all emails.
This is why email encryption is so complicated
In theory, all mails are open.
In theory, encryption of e-mails is also a good thing: The sender encrypts the message with the recipient's public key, only character chaos is displayed on the way, and only the recipient can use his or her private key and the appropriate password to decrypt the message again. The so-called principle of end-to-end encryption. All of this happens in the virtually unbreakable RSA or AES encryption method . But what sounds so good in theory is not so easy in practice. On the one hand, both sides must already use PGP so that they can communicate in encrypted form (and this is not supported by default by Google, Apple, Microsoft and co., So that you have to take action yourself and help yourself with apps and plug-ins). On the other hand, the sender does not always know exactly whether the recipient's key is still up-to-date or whether it belongs to the recipient at all. If you have avoided these cliffs and exchanged the keys with the people you are talking to, PGP is actually child's play! Check the box here; enter a password there - and you can communicate in an NSA-safe manner!
GnuPG, OpenPGP, S / MIME ...
But why is mail encryption complicated? It starts with the fact that there are several standards: OpenPGP and s / MIME are currently the most important. PGP emerged as the first process and when this became commercial, the free offshoot OpenPGP, compatible with the original PGP, was developed, which nowadays is primarily used by private users (when the article refers to PGP for the sake of simplicity, then OpenPGP is meant) . s / MIME, on the other hand, is more of the business variant that requires official certification. In this article we therefore want to concentrate on the OpenPGP standard. GnuPG is a free Unix tool for mail encryption by OpenPGP. User-friendly clients are available for Windows as well as Mac and Linux systems (https://www.heise.de/download/product/gnu-privacy-guard-gnupg-1677). Additional apps are required for mobile devices: For example, iPGMail on iOS and under Android OpenKeychain and a suitable mail app such as the K-9 Mailer or Kaiten. In principle, this means that mail encryption is available on all major operating systems and end devices.
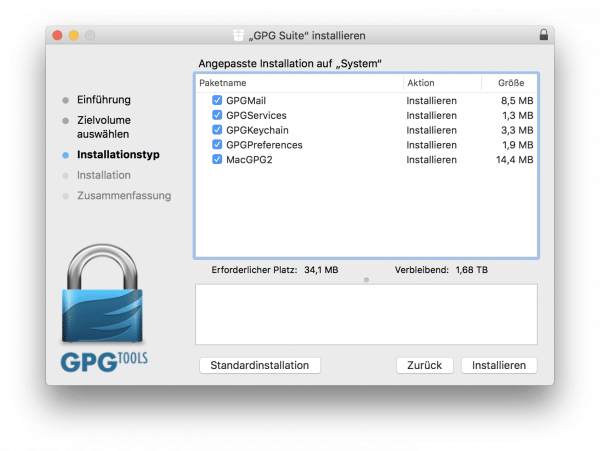
The Key
Pair Thing To get started, you first need to create a key pair for your mail account . This is very easy with the software tools: you specify the account to be encrypted and an encryption strength, as well as a password. You can then receive encrypted messages or sign your mails. Signing means that the e-mail is sent unencrypted, but the recipient recognizes from the signature that it really came from you and that the content was not manipulated. Encryption, on the other hand, encrypts the message completely, it can only be read if the recipient can decrypt it. And this is where the key pairs come into play: There is one private and a public key . As the name suggests, the private key must remain private, i.e. it must be on your computer. The public key, on the other hand, is uploaded to a key server and can be accessed publicly..
Why this effort?
The principle behind this method is an asymmetrical encryption method : The public key on the key server allows anyone to send you an encrypted message that only you can decrypt with your private key. Conversely, this means that you can only send encrypted messages to people who have also already created a key pair and uploaded a public key. Which means that the core problem of mail encryption is also obvious: Mail can only be encrypted and decrypted between participants in the PGP / OpenPGP system - and if someone misplaces their private key or forgot the password for their key, they can no longer read the message. Modern GnuPG clients can check whether a public key is available, but they cannot check whether the recipient is still using the tool and can decrypt their emails.
The matter of identity
Another problem is that anyone can create keys - under any name and for any e-mail address. The identity is practically not verified by the computer. This is where the "web of trust" comes into play . The public keys are "signed" for each other, thus creating a kind of "networked trust". You can do this in a personal exchange with your friends or business partners, or at a crypto party that takes place precisely for the purpose of this mutual certification. In the broader context, the c't magazin supports PGP / GPG with the free c't crypto campaign . Here, the c't serves as a certificate authority ( CA) a high level of trust , because it has been actively advocating PGP / GPG for over 20 years. You can obtain a signature by applying for certification and proving your identity by submitting the application in person with identification with a current ID card or passport. If you then verify the specified email address, you will receive a signature so that someone who doesn't have a public key but knows the crypto campaign can tell by signing it that you are who you say you are. To check the authenticity, the "fingerprint" (a unique number for each key) of the CA key of the crypto campaign is printed in the c't imprint. You can submit the application either at selected trade fairs or Heise events, or on Wednesdays between 4.30 p.m. and 5.30 p.m. in the Heise publishing house in Hanover. You can find more information about the crypto campaign here: https://www.heise.de/security/dienste/Krypto-Kampagne-2111.html
The thing about webmailers
Not every webmailer can use OpenPGP . Via Googlemail, OpenPGP is supported rather half-heartedly and explicitly unofficially with E2Email, and that exclusively through a Chrome plug-in. With GMX and Web.de it looks much better. However , PGP can be used relatively comfortably via the Mailvelope plug-in for Firefox and Chrome. However, due to operating system or software updates, it can always happen that the OpenPGP plug-ins do not work for a while until an update is available for them..
High technical hurdle
The technical hurdles and the tolerable support from the largest mail providers are reasons that mail encryption has not yet become widely accepted in the private sector. At least on the way between you and your mail provider, the mail is protected on a small scale via Transport Layer Security , or TLS for short. This has long been the norm with all common webmail providers in the browser. It can be recognized by the small lock in the URL line : Your computer and the mail server use it to negotiate an encryption that protects the messages on the way there.
You can also activate TLS in your mail program if you are using a program such as Apple Mail, Thunderbird or Outlook. The advantage of this solution is that it always works - and doesn't require any further setup. TLS significantly increases the security of e-mails, but it is not an encryption technology that is as strong as OpenPGP , as it does not secure the entire transport route. Until someone invents a simple, global implementation of mail encryption, the following applies: take action yourself and seal your mail traffic against prying eyes or treat e-mails like postcards, then you have nothing to fear.