The security gaps Meltdown and Specter are currently causing a stir in the IT world, as the affected processors are built into billions of computers. In the meantime, both hardware and software manufacturers have reacted and released the first security updates. We'll show you how to find out which processor is built into your PC. We will also introduce you to two tools with which you can check the protection status of your computer.
Hardware and software manufacturers have been working at full speed on patches and security updates since the processor security gaps Meltdown and Specter became known. You can find a list with links to the safety instructions from the hardware and software providers here. The manufacturer Intel, whose processors are particularly badly affected by the security vulnerabilities, has published a list of the processors at risk .
Which processor is built into my PC?
To find out whether your PC is at risk, you need to know which processor is built into your computer. There are two ways you can do this:
1. Key combination
Use the key combination [Windows] + [Pause] to open the system properties. There you can see which processor (CPU) is installed in your computer. If you have a laptop with no pause button, you can do the following to read your CPU:
2. DirectX
Another way of displaying your built-in processor is via the DirectX diagnostic program. To do this, first press the key combination [Windows] + [R] and enter the command dxdiag in the Run field . Confirm with " OK " and you will be shown an overview with the most important system information. You will also find a list of your installed CPU there..
Check the protection status of your PC
You can find out whether your PC is still at risk with tools such as SpecuCheck and PowerShell .
SpecuCheck
- Download SpecuCheck, e.g. from heise Download: https://www.heise.de/download/product/specucheck
- Then open the command prompt ( e.g. by typing cmd into the Cortana search ).
- Then navigate in the command prompt to the directory in which you have saved SpecuCheck, e.g. cd C: \ Users \ Anna \ Desktop . Confirm with Enter .
- Now enter the command Specucheck.exe and confirm again with Enter . You will then be shown whether your system has already received a security update (patch).
PowerShell
- Open PowerShell as administrator by pressing [Windows] + [X] and then selecting the entry " Windows PowerShell (administrator) ". If the entry is missing, you can also enter powershell in the Cortana search and select Windows PowerShell by right-clicking " Run as administrator " on the result .
- First enter the command Set-ExecutionPolicy -ExecutionPolicy RemoteSigned in PowerShell and confirm with Enter . You are now allowed to download scripts.
- You download the check script using the Install-Module SpeculationControl command . Confirm your entry again with Enter .
- During the download process you have to confirm the process several times with a Y for "Yes".
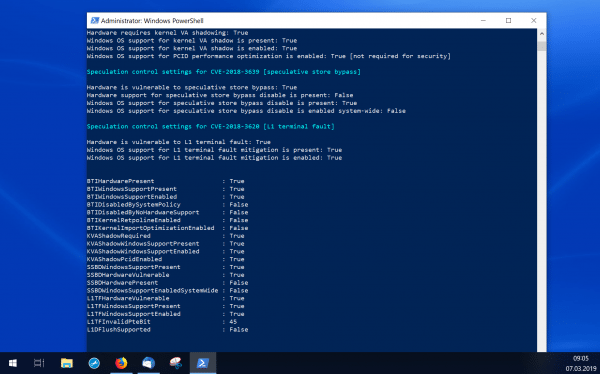
- You then start the script with the Get-SpeculationControlSettings command . You will then be shown whether your system is protected. The following is important:
For CVE-2017-5715, every point should be set to " True ".
For CVE 2017-5754, the first point is probably "True" anyway. The other points should then also be set to " True ".
For CVE-2018-3639, the first point is likely to be " True ". You don't have to worry about this. It just means that, in theory, your hardware can be vulnerable to this type. It is important here that the third point "Windows OS support for speculative store bypass disable is present" on " True This means that Windows protection against this type is active.
The first point in CVE-2018-3620 should be set to " False " if possible . But don't worry, if this is set to "True", it is important to that the other two points are set to " True. " Your computer is susceptible to the type " L1 terminal fault ", but Windows protects you from it.