Create an SSH key under Linux and macOS: Here's how 1st step: 2nd step: 3rd step: 4th step: 5th step: How to create an SSH key on Windows 1st step: 2nd step: 3rd step: 4th step: 5th step: 6th step: What to do with the SSH keys
SSH, short for “Secure Shell”, is a practical matter: Using a terminal - or in Windows systems with the help of the small PuTTY tool - you can conveniently manage another computer remotely via SSH via the command line. This is always practical when Unix-based systems - such as a media center PC, a craft computer, a server or web server or a NAS - are involved. Thanks to SSH, the systems do not need a user interface, a connected keyboard, mouse or screen: SSH takes care of the terminal control remotely, conveniently from the laptop or PC. In order for this to work smoothly and securely, an SSH key should be set up for what is known as public key authentication: This consists of a key pair in the form of a public and a private key and ensures a secure login.
Create an SSH key under Linux and macOS: Here's how
In order to create an SSH key under Unix systems such as Linux or macOS, the so-called terminal is important. This is the command line within the graphical user interface of the system. If you use Linux without an interface, you can also use the respective shell - there is no difference here.
1st step:
 Open a terminal window. You can find this in most Linux interfaces in the " Start menu " or in the menu bar . On macOS you can find it in the folder / Applications / Utilities / .
Open a terminal window. You can find this in most Linux interfaces in the " Start menu " or in the menu bar . On macOS you can find it in the folder / Applications / Utilities / .
2nd step:
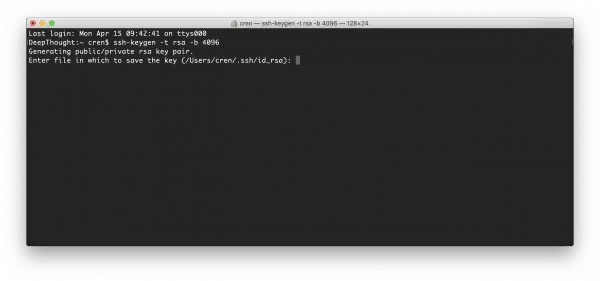 Under Linux, you may have to install OpenSSH in more puristic distributions , macOS and most standard distributions already have the SSH key creation on board. First, enter the command ssh-keygen -t rsa -b 4096 . This creates a key according to the RSA cryptosystem with a length of 4096 bits. This means that the key can hardly be cracked using brute force.
Under Linux, you may have to install OpenSSH in more puristic distributions , macOS and most standard distributions already have the SSH key creation on board. First, enter the command ssh-keygen -t rsa -b 4096 . This creates a key according to the RSA cryptosystem with a length of 4096 bits. This means that the key can hardly be cracked using brute force.
3rd step:
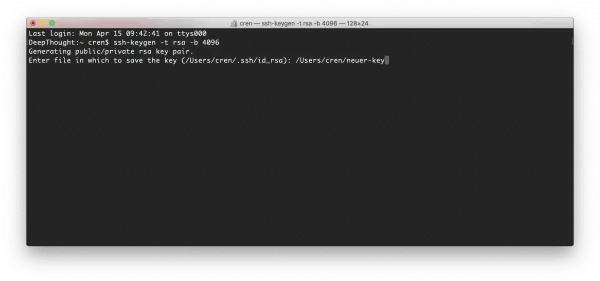 The computer now asks in which file the key should be stored. It is best to enter a new file that is clearly named. The default setting in macOS is that the key will otherwise end up in the standard file, and that is confusing; especially since the “.ssh” folder is hidden. Confirm with the Enter key .
The computer now asks in which file the key should be stored. It is best to enter a new file that is clearly named. The default setting in macOS is that the key will otherwise end up in the standard file, and that is confusing; especially since the “.ssh” folder is hidden. Confirm with the Enter key .
4th step:
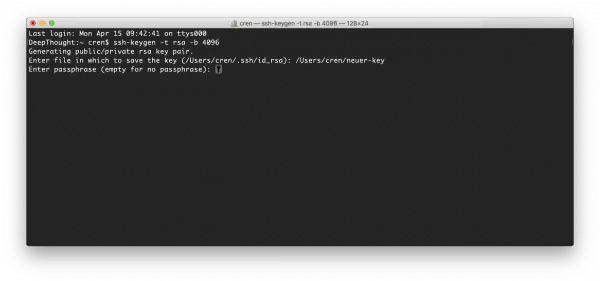 You can now also assign a passphrase for even more security , but this is not absolutely necessary. If you want to use a passphrase for the key, you can enter it and then have to confirm it. Otherwise, you can skip this option by pressing Enter. At this point we create a key pair without an additional passphrase.
You can now also assign a passphrase for even more security , but this is not absolutely necessary. If you want to use a passphrase for the key, you can enter it and then have to confirm it. Otherwise, you can skip this option by pressing Enter. At this point we create a key pair without an additional passphrase.
5th step:
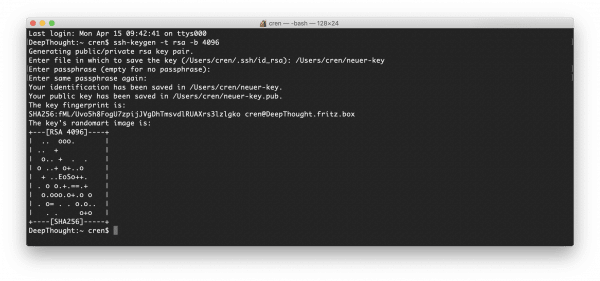 That's it: the key pair has been created and is in the file specified in step 3. You can open these later with a text editor (in Terminal vi, under macOS any editor, such as CotEditor ) to view and use the key pair .
That's it: the key pair has been created and is in the file specified in step 3. You can open these later with a text editor (in Terminal vi, under macOS any editor, such as CotEditor ) to view and use the key pair .
How to create an SSH key on Windows
1st step:
 The creation of an SSH key is also not a problem under Windows. But first you have to install the free PuTTY tool . Then you can start creating the key.
The creation of an SSH key is also not a problem under Windows. But first you have to install the free PuTTY tool . Then you can start creating the key.
2nd step:
 Do not open PuTTY, but rather the installed PuTTYgen . You can find this by entering "PuTTYgen" in the Cortana or Windows search.
Do not open PuTTY, but rather the installed PuTTYgen . You can find this by entering "PuTTYgen" in the Cortana or Windows search.
3rd step:
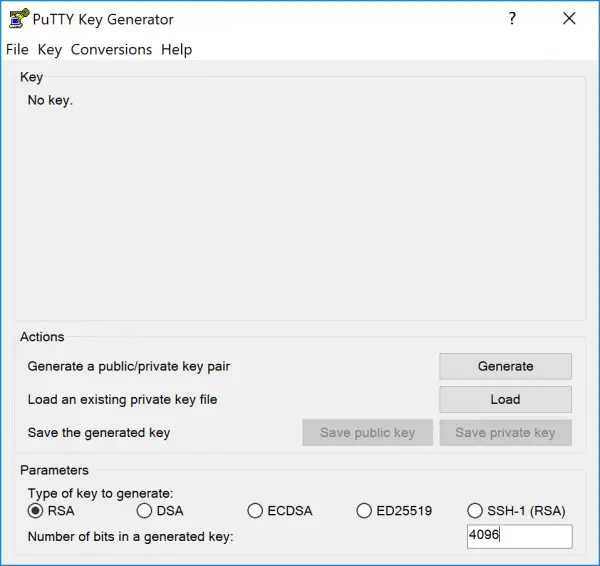 Now set the necessary parameters in the PuTTYgen interface. The following parameters are required to create a key: RSA and a bit length of 4096 . Then click on " Generate ".
Now set the necessary parameters in the PuTTYgen interface. The following parameters are required to create a key: RSA and a bit length of 4096 . Then click on " Generate ".
4th step:
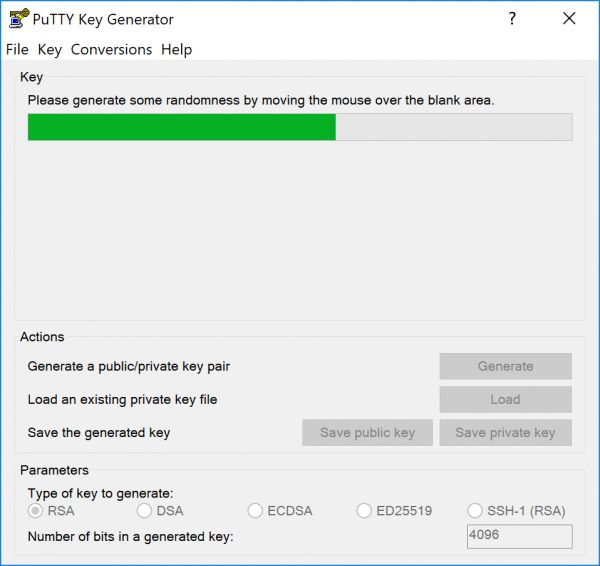 PuTTY now creates the key. For the random generator, move the mouse over the area below the bar until the creation is complete.
PuTTY now creates the key. For the random generator, move the mouse over the area below the bar until the creation is complete.
5th step:
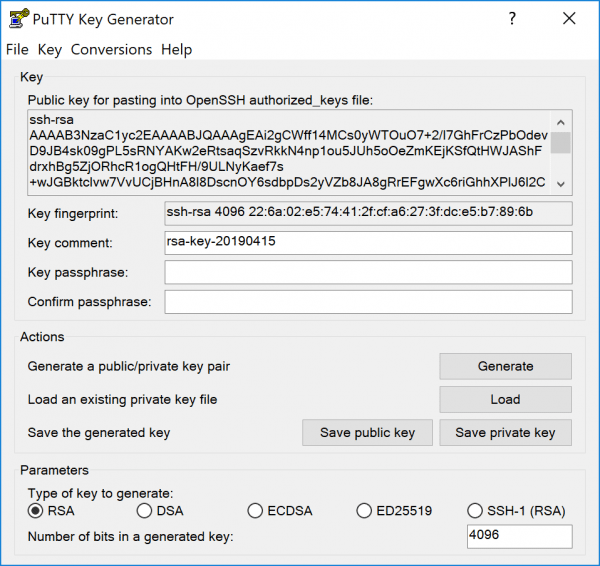 The SSH key has now been created and is displayed. You can also create a passphrase for the key in the "Key passphrase" field , but we will not do this in our example.
The SSH key has now been created and is displayed. You can also create a passphrase for the key in the "Key passphrase" field , but we will not do this in our example.
6th step:
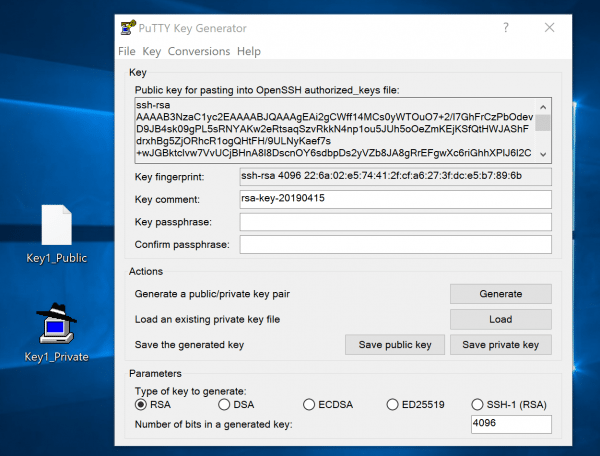 Click “ Save Public Key ” to save the public key. Then click on “ Save Private Key ” to also save the private key. Put the pair in a folder and be sure to use meaningful file names . You have now generated the key pair and can then use it.
Click “ Save Public Key ” to save the public key. Then click on “ Save Private Key ” to also save the private key. Put the pair in a folder and be sure to use meaningful file names . You have now generated the key pair and can then use it.
What to do with the SSH keys
Once the key pairs have been created, nothing stands in the way of their use. Since the creation took place on the "control computer", i.e. the laptop or PC, the public key still has to be copied to the server. First you have to log in to the server and then store the key there. The command required for this in the terminal is:
ssh-copy-id -i ~ / path / to / key file user @ server
The paths and users must of course be adapted to your conditions..
You can then contact
ssh -i ~ / path / to / key file user @ server
log on to the server. A password is no longer required in the set setting, since the private and public key match. The command line may complain that the key is not available. In this case you have to move the file with the private key to the hidden user subfolder .ssh on your "control system".