You can use your GitHub repository from the terminal without constantly entering your username and password. In the following, we will show you how to set up an SSH key for passwordless login.
What is this exactly?
Typically, you will initially access your GitHub repository the "standard way": you clone the HTTPS link and then enter your username and password when you upload / push changes. If you push a lot, it is more of a nuisance.
If you want to work with keys instead, clone the repository using the alternative SSH link and a pair of keys will do the authentication. You create the key pair from private / secret and public key locally, the public key is stored on GitHub. With such "deploy keys" users can clone / deploy private repositories without entering a password. However, you can also assign write permissions to the deploy keys and thus set up a simpler workflow..
Create and register the SSH key
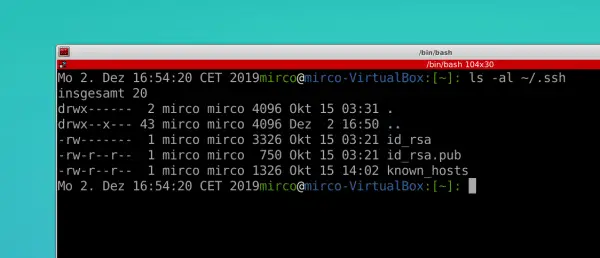
First you should check whether SSH keys already exist. The command " ls -al ~ / .ssh " does this in the terminal , because the keys are simply in the hidden SSH folder in your user directory. The most common name combination to be found here is " id_rsa " for the private and " id_rsa.pub " for the public key.
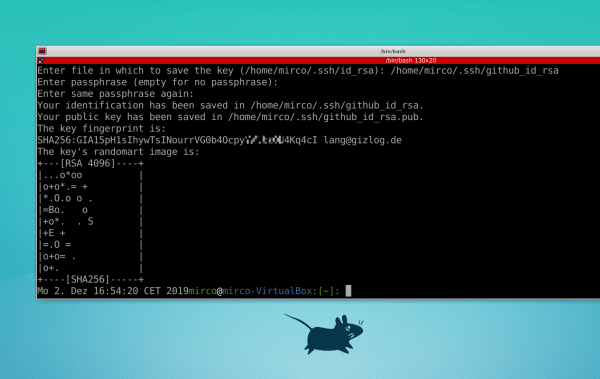
Now create a new key pair with the following command:
ssh-keygen -t rsa -b 4096 -C "[email protected]"
" rsa 4096 " determines the encryption, the authentication takes place via your email address given on GitHub. Now follow the instructions in the terminal: First enter a name for the key. It is best to leave it with the path " ~ / .ssh " and the name pattern with " rsa.pub " in it to keep it clear. Then assign a password of your choice. However, both steps are optional; you can use the default filename and omit a password to save a little work..
In the example, keys with the names " id_rsa_github " and " id_rsa_github.pub " were created and secured with a password. First, add the new identity to the authentication agent:
ssh-add ~/.ssh/id_rsa_github
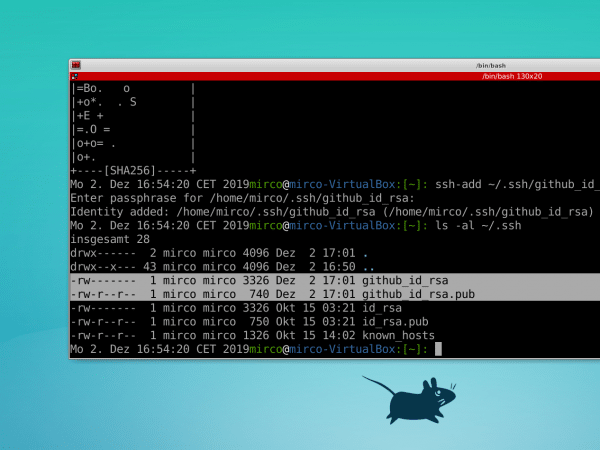
The password is now requested once, and the agent will take over the authentication for future updates. By default, Git uses the key with the default name " id_rsa ". If you want to use a different key, create the file " ~ / .ssh / config " and set read and write rights for the file owner. On this occasion you can set read-only access for the admin to the private key for security reasons:
chmod 600 ~/.ssh/config
chmod 400 ~/.ssh/id_rsa_github
Open the config file and paste the following content:
HostName github.com
IdentityFile ~/.ssh/id_rsa_github
User git
So all you have to do here is set the created private key file, or more precisely the identity, for the host github.com.
Use repository via SSH key
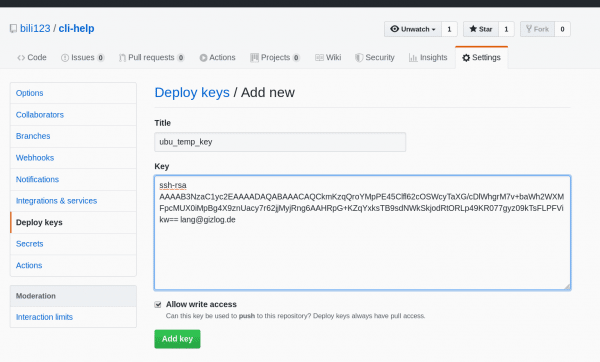
Everything is now done on your local computer, all you have to do is provide GitHub with the public key. To do this, open the required repository in the browser and call up " Settings / Deploy keys ". Use " Add deploy key " to create a new key. You can freely choose the name and copy the content of the public key file into the " Key " field, ie " ~ / .ssh / id_rsa_github.pub ". The content of the private key is never entered anywhere, so make sure you have the right files! Then save the deploy key and return to the overview with your new key.
In the terminal you can now clone your repository using the SSH link on the repo start page. If the repo is already available locally, simply test this with a short " git pul l". If everything went well, you will now receive the updates without further signing up. If you visit GitHub again in your browser and go to the Deploy Keys page, you will also see a status message stating when the key was last used. And of course you can also create multiple keys for multiple users or computers.
tip : Anyone who comes to your computer can of course also (write) access the linked repositories if the SSH key is set up without a password. You can, however, make do with a simple password. On the one hand, you save yourself at least entering the username. On the other hand: If you are away from the computer for a long time, you will lock it anyway. If the computer is stolen, you can easily remove the deploy keys in the GitHub interface. The main risk therefore tends to be that someone gets access during a short absence (coffee, toilet, in the side office, etc.) because you have not locked the computer. For a few minutes, however, a simple password that is typed in can also do, because cracking passwords simply takes time.Nevertheless, you should refrain from the first standard attempts of every hacker (or meanwhile also TV thriller viewer ...): Neither "123456" nor "Password" can be used as passwords at all. You can read how to find secure passwords in this article.