"Your data will be encrypted - pay xy Bitcoins to restore them." - a message that makes even experienced Windows users a cold sweat on their foreheads. Encryption Trojans have recently become one of the most feared IT threats of all. The so-called "ransomware", which takes the data on your PC hostage, can be a real catastrophe without a backup. The worst: There is no guarantee that the crypto Trojans will actually decrypt the data again. In an emergency, with a little luck you can help yourself - we will show you how you can pull the tooth out of encryption Trojans.
Ransomware: data recovery is at least theoretically possible
If your PC is caught by a crypto Trojan, the most important rule is: don't panic! If you have a backup of your encrypted files, you can restore them after the cleanup and avoid the greatest damage. If this is not the case, things get more complicated: There are currently no effective antidotes against many encryption Trojans. But before you initiate the payment via Bitcoin, you should at least sound out all possible ways of saving your data after all.
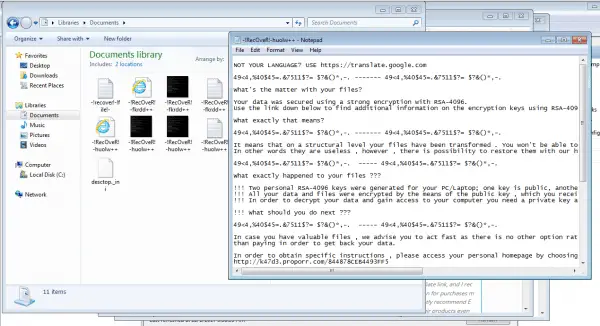 Once an encryption Trojan has struck, you no longer have access to documents and photos.
Once an encryption Trojan has struck, you no longer have access to documents and photos. Correct behavior after the infestation is difficult. Some crypto Trojans can only be removed if you do not restart your PC . The reason: In this case, the decryption is based on information that is volatile in the main memory of your PC. An example of this is WannKiwi . The program tries to rescue data that has been encrypted by the notorious WannaCry ransomware. In this case, there is only a chance of success if you have not restarted Windows after the infection. On the other hand, shutting down the PC in good time can at least interrupt the encryption , so that you can save the still unencrypted data (for example with a Linux boot CD). The "correct" procedure here simply depends on the infection ..
Identify and analyze ransomware
Before you can salvage your data encrypted by a ransomware Trojan, you must first find out what exactly it is . In many cases, all that is needed is the notification that inevitably appears on the desktop after infection with the encryption Trojans or when an encrypted file is opened. The attackers are often eager to include the technical details of the Trojan horse used in the description.
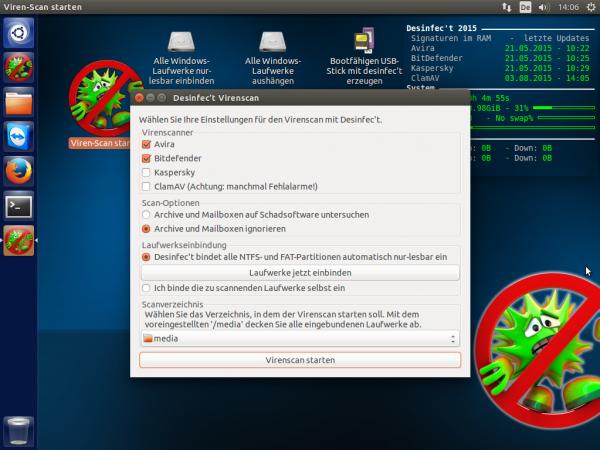 If reinstalling Windows is not an option for you, you should at least clean your PC with a live virus scanner like Desinfec't.
If reinstalling Windows is not an option for you, you should at least clean your PC with a live virus scanner like Desinfec't. As a rule, the Trojans do not prevent access to your browser and a Google search - after all, you “should” download the Tor browser in order to pay the Bitcoin ransom for your PC via the Darknet. A search on Google for the name of the ransomware is often a sensible first step on the way to possible data recovery..
If the information is not enough for you, you should take a look at the " ID Ransomware " service . The online tool offers several approaches to detect the ransomware on your PC. You can use the “ ransom note” button to upload the text or image file that a crypto Trojan usually places on the desktop or in the encrypted directories. Alternatively, you can use the " Encrypted file " button to transfer such a file to ID ransomware. The service now analyzes the encryption and tries to present possible solutions . Ideally, the website will provide you with a solution to rescue the hijacked data. If this is not the case, you can of course research other solutions - in the worst case, however, you have to expect that your files will remain encrypted.
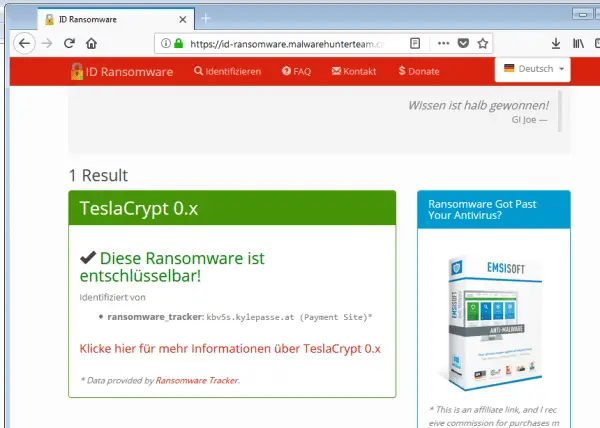 Good luck: the analysis has shown that you can potentially recover the encrypted data.
Good luck: the analysis has shown that you can potentially recover the encrypted data. Ransomware: download decryption tools and rescue data
With the appropriate amount of luck in misfortune, the ransomware analysis shows that you can salvage the encrypted data. If this is the case, ID ransomware provides you with the necessary information and offers you a suitable decryption program for download . Once a Trojan's decryption routine has been cracked, data recovery is usually very easy. Most of the tools - in our example, the AVG decryptor for the Tojaner TeslaCrypt - are usually in the form of a wizard that makes restoring easy. When in doubt, a Google search will provide further instructions on how to defuse the ransomware.
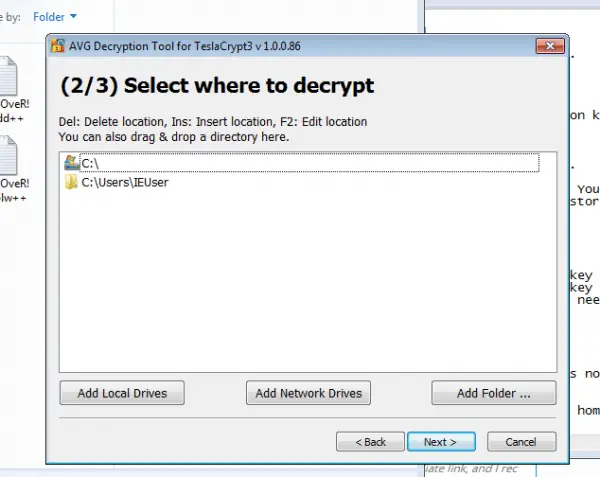 Once the ransomware's encryption has been overcome, recovery is delightfully easy.
Once the ransomware's encryption has been overcome, recovery is delightfully easy. In addition to ID ransomware, there are a number of other contact points that collect information and, above all, tools for rescuing crypto Trojans. We recommend visiting NoMoreRansom ( https://www.nomoreransom.org/de/index.html ), The Windows Club ( http://www.thewindowsclub.com/list-ransomware-decryptor-tools ) and the Security news from Heise Security .
Get rid of encryption Trojans for good
Even if you can recover files hijacked by an encryption Trojan, it is important to make sure that you get rid of the malware yourself . You can of course rely on the help of your virus scanner or additional scans by programs such as Malwarebytes Anti Malware or a live CD virus scanner such as Heise Desinfec't . However, only a clean reinstallation of Windows provides you with real certainty that Windows has been freed from the malware . Alternatively, you can - if available - import a backup from a point in time at which your Windows installation was not yet infected.
 If reinstalling Windows is not an option for you, you should at least clean your PC with a live virus scanner like Desinfec't.
If reinstalling Windows is not an option for you, you should at least clean your PC with a live virus scanner like Desinfec't. In the future, you should do everything you can to avoid re-infection . We have summarized tips and strategies against encryption Trojans for you in this article. Because: Even if there is a chance of saving data after being infected with a crypto Trojan, it is not realistically too high. So the best protection against ransomware is efficient prevention .