Blackmail Trojans, so-called "ransomware", encrypt the files on your hard drive and only release them again when you transfer a "ransom" - if at all. Under the names WannaCry, Bad Rabbit or Locky, the Trojans terrify Windows users. But you can protect yourself from the virtual hostage-taking! We'll show you how you can protect Windows 10 against ransom trojans.
Use virus protection and Windows updates
Basically, the same security measures apply to ransomware as to "traditional" malware: Do not open any files that you have obtained from unknown e-mail senders or from possibly unsafe download sources and keep your Windows up to date using the update function . Windows 10 automatically installs critical security updates. To ensure that the system is up to date, open "Settings" from the start menu. Here you navigate to the "Update and Security" area and manually search for updates if necessary. You can find detailed instructions for performing manual updates with Windows 10 in this tips + tricks article. Microsoft regularly closes various gateways for malware via patches - it is negligent to forego the corresponding updates.
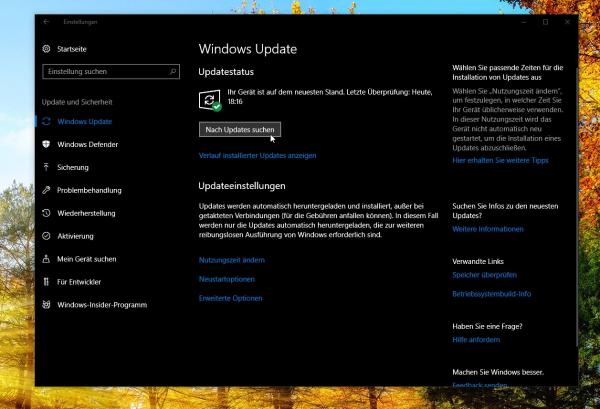 Windows is only safe if Windows is up-to-date - so install available Windows updates as quickly as possible.
Windows is only safe if Windows is up-to-date - so install available Windows updates as quickly as possible. Also a running virus protection is a must . In the meantime, even the Windows Defender integrated in Windows 10 ensures a decent level of security. Current security suites from companies such as Eset, Bitdefender or G-Data go one step further. In their current versions, these often offer extended protection against blackmail Trojans. The virus scanners warn when running programs want to manipulate system-critical folders and prevent access to the data..
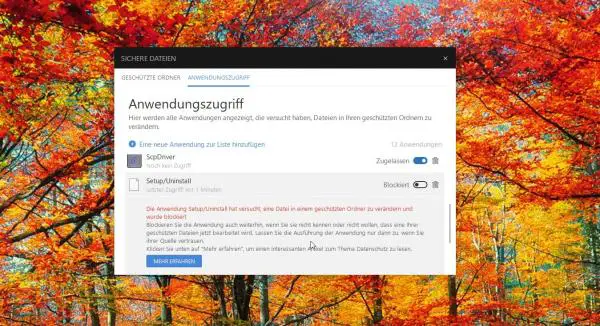 Current security suites such as BitDefender 2018 protect system folders from encryption.
Current security suites such as BitDefender 2018 protect system folders from encryption. How to use the integrated folder protection of Windows 10
With the Fall Creators Update published in September, Windows 10 received a native protection mechanism against encryption Trojans. The "Protected Folders" function ensures that programs - and thus encryption Trojans too - can no longer manipulate certain areas on the hard drive. In practice, this means a little less convenience, but important folders are safe from ransomware.
If you have already installed the update, you will need to activate the protection manually . To do this, proceed as follows:
1st step:
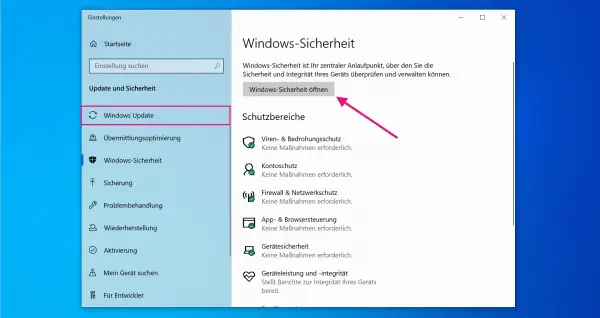 To do this, open the Windows 10 settings and navigate to "Update and Security " > " Windows Security " > " Open Windows Security ".
To do this, open the Windows 10 settings and navigate to "Update and Security " > " Windows Security " > " Open Windows Security ". 2nd step:
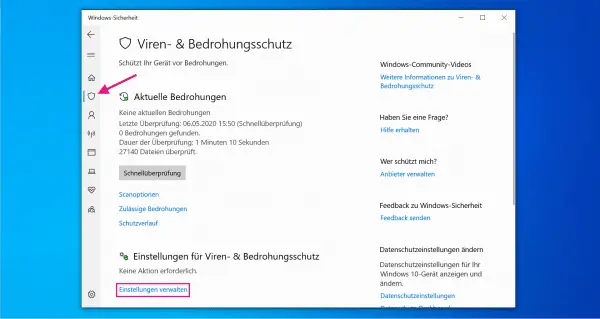 In the window that opens, click on the left on the "Virus and threat protection" icon and then on the " Manage settings " button under Virus and threat protection settings.
In the window that opens, click on the left on the "Virus and threat protection" icon and then on the " Manage settings " button under Virus and threat protection settings. 3rd step:
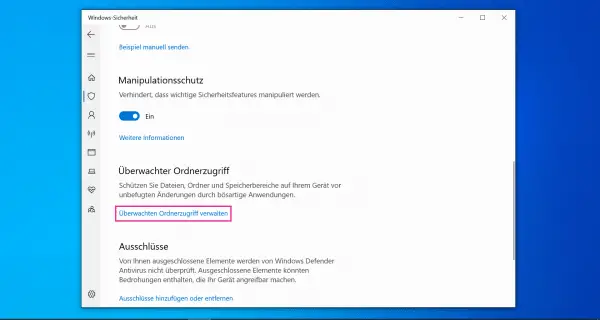 In Settings, scroll down to the " Monitored Folder Access " section. To protect your files, first click on " Manage watched folder access ".
In Settings, scroll down to the " Monitored Folder Access " section. To protect your files, first click on " Manage watched folder access ". 4th step:
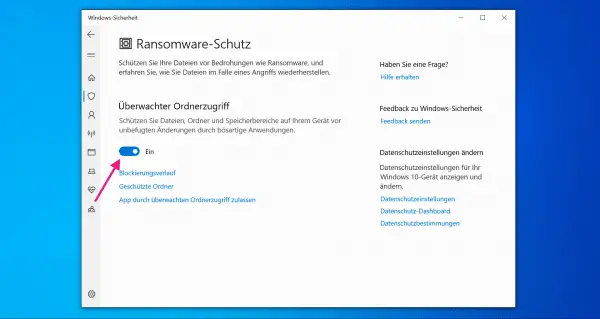 To enable monitored folder access, switch the option from " Off " to " On ".
To enable monitored folder access, switch the option from " Off " to " On ". 5th step:
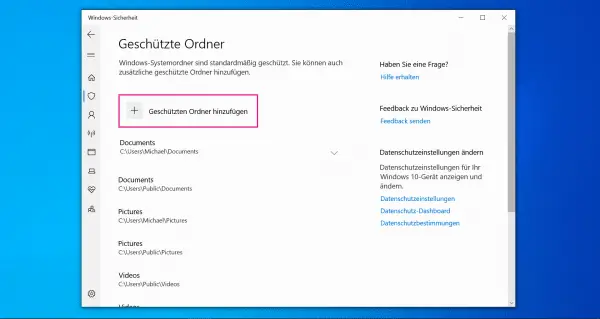 Using the links " Protected folders " and " Allow app through monitored folder access ", you can now specify in detail which folders Windows 10 should protect against changes. To do this, click on "Add Protected Folder". You can also give your favorite programs (such as Office tools) authorization to create, edit or delete files in the folders.
Using the links " Protected folders " and " Allow app through monitored folder access ", you can now specify in detail which folders Windows 10 should protect against changes. To do this, click on "Add Protected Folder". You can also give your favorite programs (such as Office tools) authorization to create, edit or delete files in the folders. Perform regular backups
Despite all precautionary measures: The best protection against encryption Trojans is and remains a current Windows backup . In an emergency, you can restore a functioning Windows environment without malware with little effort and only lose the data that you have edited since the last backup. Windows 10 has two backup solutions on board in the form of the file version history and the integrated image backup - unfortunately, both are not activated at the factory. To change this, open the system settings and navigate to the "Update and Security - Backup" menu. Here you can use the wizard to set up the Windows 10 file history. The link “Switch to backup and restore (Windows 7)” takes you to the image backup, which is still based on the older Windows versions. Here, too, an assistant will help you set up the backup.A detailed guide on how to create backups with Windows 10 can be found in this article..
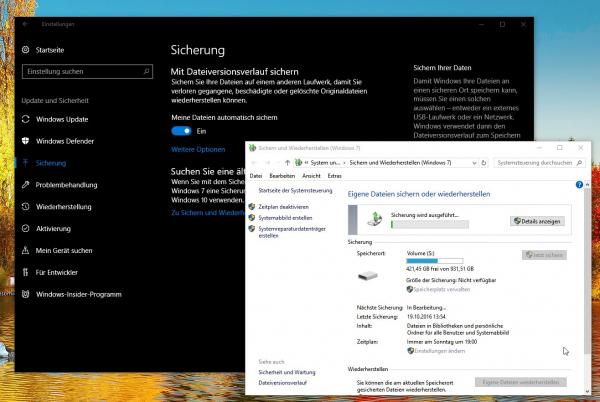 You can use Windows standard tools to make backups that protect you from data loss.
You can use Windows standard tools to make backups that protect you from data loss.
If the possibilities of the Windows standard tools are not enough for you, you can also switch to third-party tools. Even free solutions such as Macrium Reflect or EaseUS ToDo Backup offer sufficient functions to back up Windows hard drives and restore them if necessary.
 Free backup tools are sufficient to be prepared for an emergency Trojan horse.
Free backup tools are sufficient to be prepared for an emergency Trojan horse. Important : Make sure to use an external target (such as a USB hard drive) for the backup that is not permanently connected to the PC. Since modern encryption Trojans are increasingly plunging themselves onto USB and even network drives, this is the only way to prevent your backups from being hijacked as well.
Back up important data in the cloud
Cloud storage services such as Dropbox, OneDrive or Google Drive offer excellent protection against encryption Trojans . The reason: Even in the free offers, almost all services allow you to restore previous versions of a file. In practice this means: If an encryption Trojan hijacks your files, you can retrieve them via the online storage without paying a cent. The procedure is usually always the same: Log into your cloud account via your browser. Here you navigate to the folder with the encrypted files and call up the options via the menu or a right-click. Now look for an option like “Restore previous version” or “Version history” and get the unencrypted file back.
If you are reluctant to entrust your personal documents to commercial providers such as Dropbox or Google Drive, you can also host your own cloud . Solutions such as OwnCloud or NextCloud allow you to set up self-hosted cloud storage on rented web space. This means more effort, but also protects privacy.
Encryption Trojans: What To Do If It's Already Too Late?
As you can see, with a little effort, you can protect yourself efficiently against the dangers of blackmail trojans. But what if it's too late and your PC has caught some nasty encryption malware? In this case, you should of course immediately stop using the infected computer and remove it from your home network .
The second important rule is: Under no circumstances should you comply with the demands of the virtual hijackers! There are countless cases in which ransomware victims have paid the required Bitcoin sums but still haven't got their data back. If an encryption Trojan has caught your PC, you should therefore remain calm. Ideally, security experts develop a tool that can bypass the encryption routines and secure your data.
 New blackmail Trojans keep popping up, for example Bad Rabbit. The procedure is almost always the same.
New blackmail Trojans keep popping up, for example Bad Rabbit. The procedure is almost always the same. The No More Ransom initiative , the Federal Office for Security and Information Technology and the security reports on Heise Security provide first aid in the event of ransomware infestation . There is no guarantee that you will be able to free your PC from the clutches of ransomware, but at least there is a chance.
If that is not the case, you will not get around a clean reinstallation of Windows 10 for better or worse . Ideally, you can then restore your data from the cloud or a backup. If this is not the case, you can at least provide for the future and secure your data from Locky, WannaCry and their descendants.